I recently upgraded my DNS server to Debian Jessie. In fact I reinstalled it from scratch and used puppet to install and configure all the required components. This DNS server, running bind9, is the authoritative nameserver for nethuis.nl.
nethuis.nl uses DNSSEC. To apply DNSSEC I used dnssec-tools, which gives you tools like zonesigner, rollerd and donuts to sign, roll and check your DNSSEC enabled zones. Two years ago I had a hard time setting this up, hitting various bugs in dnssec-tools 1.13-1 from Debian Wheezy. I ended up running a quite stable setup after packaging dnssec-tools 1.14 and using a patched version of zonesigner that didn’t increase the serial of the zone.
While installing the same setup on Debian Jessie, I noticed that dnssec-tools wasn’t in Jessie because of a bug in rollerd. I decided to install the dnssec-tools 1.14 package I used before on Debian Wheezy. This all seemed fine until I receive this email from my daily donuts run:
undefined method Net::DNS::RR::new_from_hash at /usr/lib/x86_64-linux-gnu/perl5/5.20/Net/DNS/RR.pm line 791.
Net::DNS::RR::AUTOLOAD("Net::DNS::RR", "rname", "hostmaster.nethuis.nl", "serial", 2014081039, "class", "IN", "expire", 1814400, ...) called at /usr/share/perl5/Net/DNS/ZoneFile/Fast.pm line 201
Net::DNS::ZoneFile::Fast::parse("file", "nethuis.nl.signed", "origin", "nethuis.nl.", "soft_errors", 1, "on_error", CODE(0x4ec0698)) called at /usr/sbin/donuts line 338
This thread indicated there are more related issues in the dnssec-tools package.
Time to re-evaluate. Debian Jessie is frozen, dnssec-tools didn’t get in and there is not much conversation going on in bugreport #754704 that kicked dnssec-tools out of testing. I also can’t update the signed zones as long as this is broken and the current signed zone is valid until 3 weeks from now. 😥
OpenDNSSEC looked like an alternative. I could have also used the tools that come with bind9 to sign, roll and check my zones. But I liked to try something new, PowerDNS.
# apt-get install pdns-server
As a previous bind9 user, the easiest way was to put all zone configuration from my original named.conf in /etc/powerdns/bindbackend.conf. I was amazed. It just worked. 😀
The nethuis.nl zone was still a pre-signed DNSSEC zone. While reading the PowerDNS documentation I found out that PowerDNS is able to do “Front-signing”, which is an amazing feature. PowerDNS does the signing part on-the-fly. There is no need to re-sign the zone every time you make a change to the zone.
First of all I changed the filename in /etc/powerdns/bindbackend.conf to the unsigned one. After that I created a database to manage the DNSSEC keys, added a line to the PowerDNS configuration to use this database and restarted PowerDNS.
# pdnssec create-bind-db /var/lib/powerdns/bind-dnssec-db.sqlite3
# echo "bind-dnssec-db=/var/lib/powerdns/bind-dnssec-db.sqlite3" >> /etc/powerdns/pdns.d/pdns.simplebind.conf
# systemctl restart pdns
I liked to keep the KSK and ZSKs I was already using for my zone, so I imported those.
# pdnssec import-zone-key nethuis.nl Knethuis.nl.+008+00754.private KSK
# pdnssec import-zone-key nethuis.nl Knethuis.nl.+008+43743.private ZSK
# pdnssec import-zone-key nethuis.nl Knethuis.nl.+008+63186.private ZSK
# pdnssec deactivate-zone-key nethuis.nl 3
# pdnssec rectify-zone nethuis.nl
# dig +short +dnssec nethuis.nl SOA
ns1.nethuis.nl. hostmaster.nethuis.nl. 2014081039 28800 3600 1814400 600
SOA 8 2 600 20150115000000 20141225000000 43743 nethuis.nl. lqH6nrHf6YPcLv2TgQgC4gOI4gOGORsmfj/LDJAhu+GpWpiFTnQGtj08 I2TocYQ0jwkoar370quZyvKNAyjTBGNUw6rOxdjbxAn8DhMpBPi7TMfq PP7NXJLkxbx2aIW9r1C0iMk5WAYbi01bEsJY014WiX+s+QdRDPwWaanZ zFI=
That’s it. I’m really happy PowerDNS integrated DNSSEC in it’s product instead of having an additional toolset to manage DNSSEC pre-signed zones.
Update
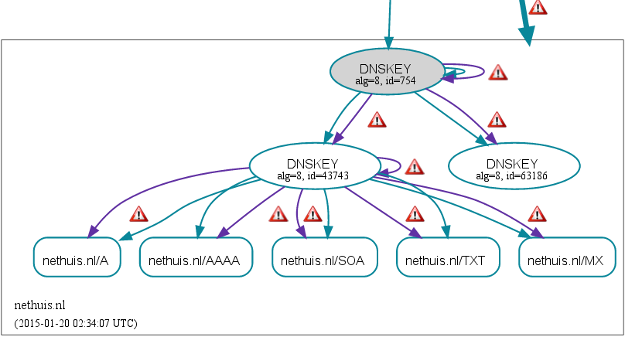
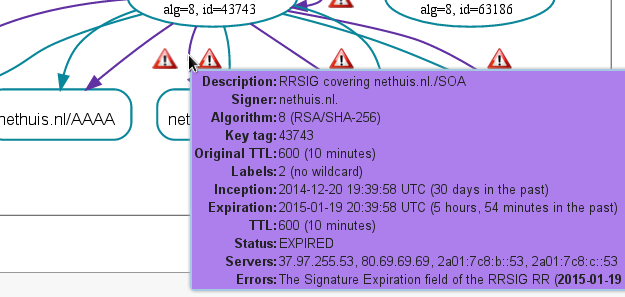
On January 19th, 20:39:59 UTC, it got completely out of hand. The images below from dnsviz.net showed me the nethuis.nl zone was expired on all the Authoritative DNS slaves.
Hovering with my mouse over the purple lines showed me the expired status:
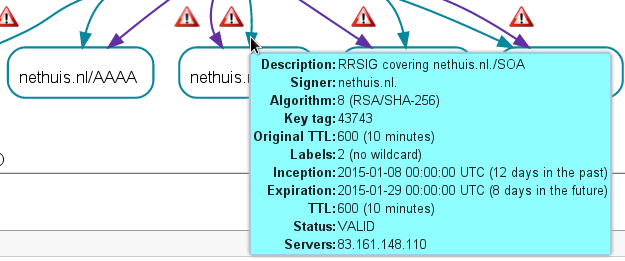
While the nethuis.nl zone hosted on the Authoritative DNS master was completely fine:
What was going on here? 😕
It was clear that the slaves didn’t transfer the zone after it was re-signed by the Authoritative DNS master. According to RFC 1996 the SOA record should be increased if you want the Authoritative DNS slaves to update their zones. This is something that was clearly not done in my case.
I found the SOA-EDIT setting. My current SERIAL is configured in the YYYYMMDDSS format, so I configured the SOA-EDIT setting to use INCEPTION-INCREMENT.
# pdnssec set-meta nethuis.nl SOA-EDIT INCEPTION-INCREMENT
This overrules the SERIAL that is configured in the on-disk zone-file. Every Thursday after the zone is re-signed the SERIAL is automatically increased and all Authoritative DNS slaves will transfer the new zone.